For many IT workers remotely involved with networking, it is quite common to need to expose your Intranet application to the outside world in a secured manner. Unfortunately, we work most of the time from private IP networks, be that at the workplace, at home or at the coffee shop. The router(s) or firewall (s) that stands between our workstation and the internet makes it harder to expose a local socket to the outside. Most of the time, this is preferable for security.
A couple of solutions you can choose now:
1. Change your router / firewall configuration to do port forwarding or NAT from public to your application. But in many cases, you wont be able to make that changes or you even do not have that options.
2. Tunneling services : either self hosting or cloud services such as:
- Ngrok
- FRP
- Localtunnel
This post is going to explore some of tunneling services I am using.
Setup & Installation
1. Download ngrok
ngrok is easy to install. Download a single binary with zero run-time dependencies. There are following versions available to download : Winodws, Mac OS X Linux Mac (32-bit) Windows (32-bit)Linux (ARM) Linux (32-bit) FreeBSD (64-Bit)FreeBSD (32-bit)
Note: Windows Ngrok is a command line tool. You will need to unzip it into a folder then use it from command line.
2. Unzip to install
$ unzip /path/to/ngrok.zip3. Connect your account
$ ./ngrok authtoken ad7FeWDimD3GTj1Hqkh7_m3BRJfhTyqfiZbBV8dAJFollowing screenshots are captured from Windows OS.
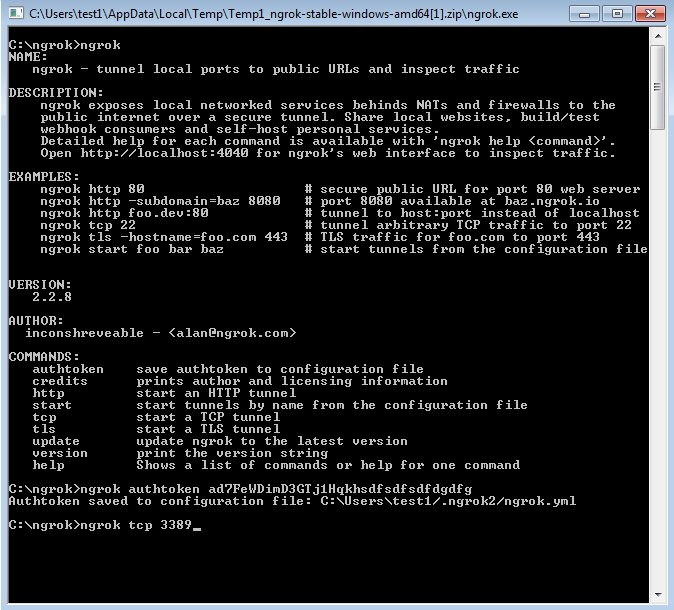 |
| Windows Command line ngrok commands |
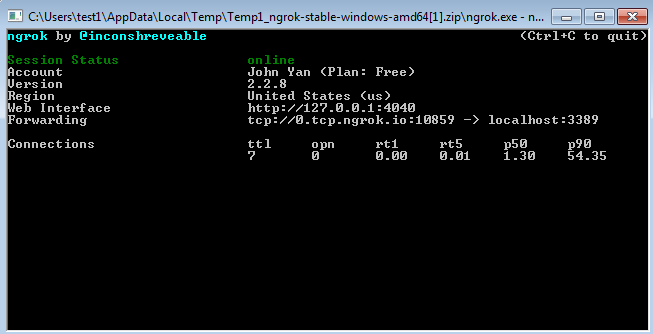 |
| Ngrok connection forwarding to localhost 3389 (Windows Remote Desktop Service) |
4. Fire it up
$ ./ngrok help$ ./ngrok http 805. Expose a local webserver
$ ./ngrok http 80$ ./ngrok start demoauthtoken: ad7FeWDimD3GTj1Hqkh7_m3BRJfhTyqfiZbBV8dAJ
region: us
console_ui: true
web_addr: localhost:4040
tunnels:
demo:
proto: http
addr: 9090
hostname: demo.mysite.com
inspect: false
auth: "demo:secret"
Youtube Video for all steps in Windows 7 :
FRP (Fast Reverse Proxy)
What is frp?
frp is a fast reverse proxy to help you expose a local server behind a NAT or firewall to the internet. Now, it supports tcp, udp, http and https protocol when requests can be forwarded by domains to backward web services.
1. Deploy frps at server side.
cd wget https://github.com/fatedier/frp/releases/download/v0.21.0/frp_0.21.0_linux_amd64.tar.gz tar -xzvf frp_0.21.0_linux_amd64.tar.gz cd frp_0.21.0_linux_amd64
vi frps.ini
[common]
bind_port = 8000
token = 'your password'
./frps -c ./frps.ini
[root@testserver1 frp 0.21.0_1inux_amd64]# ./frps -c ./frps.ini
2018/11/25 19:20:00 [I] [service.go:130] frps tcp listen on 0.0.0.0:8000
2018/11/25 19:20:00 [I] root.:o:207 Start fris success
yum -y install screen screen -S frp ./frps -c ./frps.ini
Windows zip file name is frp_0.21.0_windows_386.zip (32bit) or frp_0.21.0_windows_amd64.zip (64bit). Download address :
- https://github.com/fatedier/frp/releases/download/v0.21.0/frp_0.21.0_windows_386.zip
- https://github.com/fatedier/frp/releases/download/v0.21.0/frp_0.21.0_windows_amd64.zip
[common] server_addr = server public IP server_port = 8000 token = "your password which is same as server side" [testssh] type = tcp local_ip = 127.0.0.1 local_port = 2222 remote_port = 16316
frpc.exe -c frpc.ini
$ ./frpc -c ./frpc.ini 2018/11/25 12:21:23 [I] [proxy_manager.go:284] proxy removed: [] 2018/01/25 12:21:23 [I] [proxy_manager.go:294] proxy added: [testssh] 2018/01/25 12:21:23 [I] [proxy_manager.go:317] visitor removed: [] 2018/01/25 12:21:23 [I] [proxy_manager.go:326] visitor added: [] 2018/01/25 12:21:23 [I] [control.go:240] [3b123131341cb] login to server success, get run id [3b123131341cb], server udp port [0] 2018/01/25 12:21:23 [I] [control.go:165] [3b123131341cb] [ssh] start proxy success
2018/08/14 19:29:14 [I] [service.go:319] client login info: ip[3b123131341cb] version [0.21.0] hostname [] os [windows] arch [amd64]
2018/08/14 19:29:14 [I] [service.go:217] [3b123131341cb] [testssh] tcp proxy listen port [16316]
2018/08/14 19:29:14 [I] [control.go:335] [3b123131341cb] new proxy [testssh] success
Localtunnel allows you to easily share a web service on your local development machine without messing with DNS and firewall settings.
Localtunnel will assign you a unique publicly accessible url that will proxy all requests to your locally running webserver.
npm install -g localtunnellt --port 8000Other Remote Control Softwares
(From: Neurohazard)
- TeamViewer (可免费使用情况下,属于性能较好的解决方案, UAC穿透能力弱)
(tv 在 server 上要 licence,,而且 tv 最大的缺点是更新频繁,低版本高版本混用,闹心~在 win10 上也容易被 uac 卡住,,目前能穿透 uac 的,只有 xt800 了) - Anydesk
- Citrix gotomypc (面向企业级用户,无社区版,体验良好,微软的远程桌面功能mstsc一部分是向Citrix购买的)
- Gotoassist
- VNC
- PCAnywhere
- kdt
- xt800
- splashtop
- uvnc
- RealVNC
- 向日葵 (Windows还行, Linux糟糕)
References:
- https://news.ycombinator.com/item?id=7585056
- frp内网穿透,这个有大用处!
- https://github.com/fatedier/frp
- https://localtunnel.me
- https://ngrok.com/pricing

Or your could use a free alternative of ngrok.It provides custom domain for free Staqlab Tunnel
https://tunnel.staqlab.com
Thanks Abhishek, tunnel.staqlab.com does looks pretty good. I am going to check it out.